What Are
Embedded Containers?
Learn how containerization technology is bridging the gap between embedded and enterprise platforms to meet emerging IoT requirements.
What Are Embedded Containers?
Container technology is fundamentally changing how systems are developed, tested, deployed, and managed. The main functions of embedded containers are to wrap up applications and services with all their dependencies and to isolate multiple software components running on the same hardware.
People are most familiar with containers as part of cloud-native architectures in which applications are decoupled from the infrastructure — including hardware and operating systems — on which they are running. The benefits of this approach include being able to automate the software pipeline to remove manual errors, standardize tools, and accelerate the rate of product iterations. With a CI/CD pipeline, companies can leverage continuous integration (CI), where code changes are merged in a central repository, with continuous delivery (CD), thereby enabling the automation of the entire software delivery process and the faster delivery of high-quality software.

Container technology is fundamentally changing how systems are developed and managed.
Embedded developers can also benefit from the infrastructure-agnostic, scalable execution environment enabled by containers. Imagine a design process — from development to test to deployment to production to management — in which developers can share resources, pipelines, and results across the team. Instead of being limited by the number of development boards available, companies could exploit the elasticity of the cloud to set up multiple instances of a system on demand.
The Avionics Example
Avionics systems offer a good example of the trend toward containerization. They have evolved from fundamentally hardware-based solutions to agile, highly upgradable, software-defined infrastructures, enabling systems to incorporate new technologies on the fly, without substantial hardware replacements. Software container technology promises to be an effective means of countering cybersecurity threats through quick updates and patches, delivering benefits to both the commercial and aerospace and defense sectors.
Bridging Embedded and Cloud-Native Technologies
In spite of the benefits of containers, traditional embedded application development and deployment does differ from cloud-native architecture in significant ways:
- It is tightly coupled to specific hardware.
- It is written in lower-level languages such as C/C++.
- It interacts directly with hardware (e.g., peripherals).
- It requires specialized development and management tools.
- It tends to have a long lifecycle and stateful execution.
- It faces an increasing diversity of end hardware and software deployed in the field.
To bridge container technology to the embedded world requires that embedded development adapt to a cloud native–inspired workflow, but in a way that maintains the requirements of applications, including real-time determinism, optimized memory footprint, an integrated tool chain for cross-compiling and linking, tools for security scanning and quality assurance, and the ability to secure the build environment.
Containers for Embedded Linux
Although Linux containers have been widely deployed in data centers and IT environments, without easy-to-use pre-integrated platforms or meaningful engagement across the ecosystem, container use has been scarce in small-footprint and long-lifecycle edge embedded systems in the OT (operational technology) realm. Embedded devices such as those for industrial, medical, and automotive systems often require lightweight, reliable software with long lifecycles. Existing container technologies and platforms, like those in enterprise Linux, are often bloated or require updates too frequently to run effectively on these embedded systems.
Gartner predicts that up to 15% of enterprise applications will run in a container environment by 2024, up from less than 5% in 2020.
Initially developed at Wind River® and available on GitHub, the container technology in Wind River Linux, dubbed OverC, integrates components from the Cloud Native Computing Foundation (CNCF) and the Yocto Project to help define a comprehensive framework for building and deploying containers for embedded systems. This technology supports virtually any processor architecture and orchestration environment, removing the difficulties and lowering the barrier of entry for container usage in embedded software projects for a diverse range of applications, including industrial control systems, autonomous vehicles, medical devices and equipment, IoT gateways, radio access network (RAN) products, and a wide range of network appliances.
Containers for Real-Time Operating Systems
Container technology is complex and built for the cloud, often inhibiting usage in embedded systems, and particularly in mission-critical applications on the edge, where real-time operating systems (RTOSes) are often required.
Yet, as the complexity of applications and their supporting infrastructures create new potential attack vectors for increasingly sophisticated hackers to exploit, containers in embedded systems offer a means to deliver responsive, secure application delivery to the intelligent edge. With these capabilities, aerospace and defense organizations, energy providers, large-scale manufacturers, and medical organizations can take advantage of low-latency, high-bandwidth performance for the most challenging applications.
To leverage the promise of containers for mission-critical applications, Wind River recently launched OCI-compliant container support for VxWorks®, its market-leading RTOS, making it possible to harness the same cloud infrastructure, tooling, and workflow that developers have used in familiar IT environments. This technological advance for RTOS applications has ushered in a new era of small-footprint embedded solutions that are robust enough for critical edge-computing applications in a variety of industry sectors.
The Open Container Initiative (OCI)
To drive and unify advances in container technology, Docker, CoreOS, and other leaders in the container technology field established two specifications: a runtime specification and an image specification. The runtime specification covers the unpacking of the downloaded file system bundle — the OCI image. The file system bundle is unpacked into an OCI runtime file system bundle to be run by the OCI runtime. VxWorks adheres fully to these OCI specifications. Tools and sample code are available through the OCI and GitHub repositories.
VxWorks with OCI Compliance
Figure 1 shows the flow of creating and maintaining VxWorks containers. In a typical DevSecOps environment involving VxWorks-based containers, application code is created using a best-practices security framework. The application is released as a container to a host that is the targeted endpoint, such as a VxWorks-based device, and to the container registry. Any updates or patches to the code can be pushed to the registry, stored, and then pulled from the registry as needed by the host system, whether an aircraft, a connected car, or an electrical substation — any vehicle, medical device, IoT installation, or manufacturing facility that is using containers for code distribution.
As Figure 2 shows, once application binaries have been developed, a standard Docker file is generated. An open source tool, Buildah, creates the container image, which is a packaged file bundle containing the components of the application. The container is then pushed to the container registry and copied to the targeted hosts as well. Kubernetes provides management and orchestration of the VxWorks OCI containers.
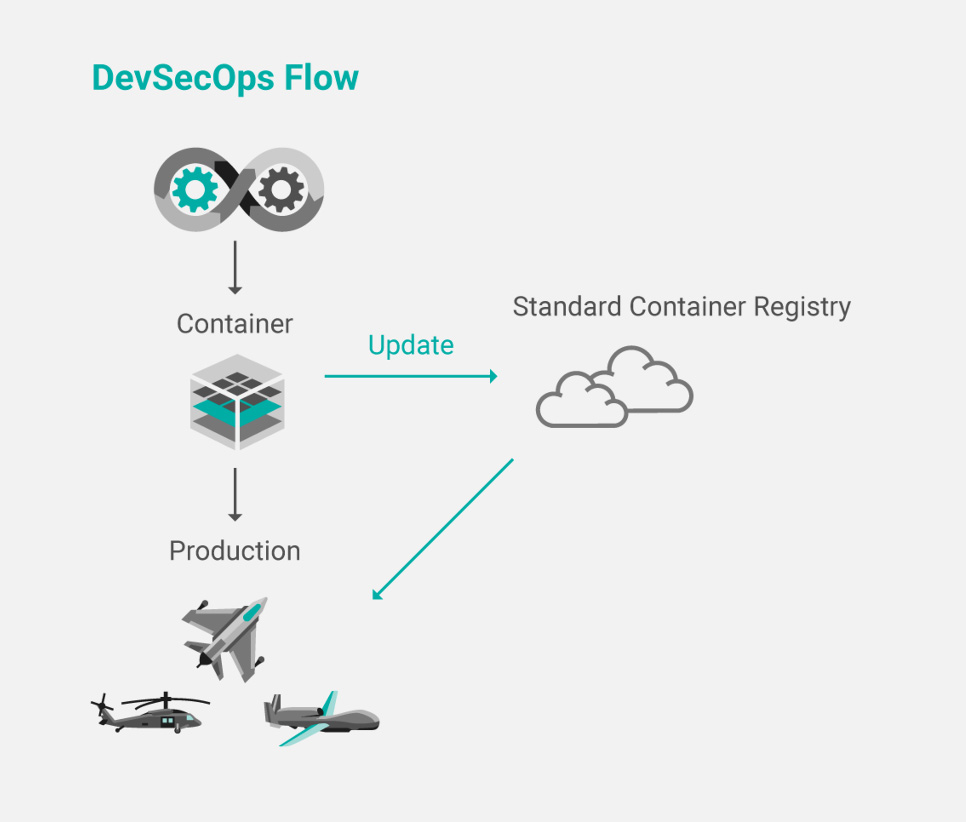
Figure 1: Production process for creating and updating VxWorks-based containers
The container registry itself — a Docker hub, Amazon ECR, Harbor, or any other OCI-compliant registry — is available for secure container access over the lifecycle of the application. Updates posted to the registry can be pulled automatically or manually by any legitimate host using the application — or set of applications — packaged in the container.
The process of distributing the containers can be handled in several different ways. For example, after landing, an aircraft can taxi to the maintenance area, connect to the airport service infrastructure, and pull any recently updated containers from the registry in the system server. The container updates will then be incorporated into the aircraft system. A vehicle equipped with modern wireless capabilities can drive past a 5G base station, receive a transmission with updates in a container, and then proceed to install those updates automatically, once the car is parked at home in the garage.
Because the technologies used in the VxWorks container implementation follow the OCI guidelines to the letter, developers know that containers they build will function reliably across infrastructures that are constructed according to the OCI standard. Proprietary solutions for software deployment, on the other hand, lack the agility and predictability of standards-based solutions and are generally unpopular in the industry for those reasons. In contrast, OCI-compliant tools — following both the image format specification and runtime specification — effectively span the ecosystem composed of container platforms and container engines, as well as standards-based cloud provider environments and on-premises infrastructures.
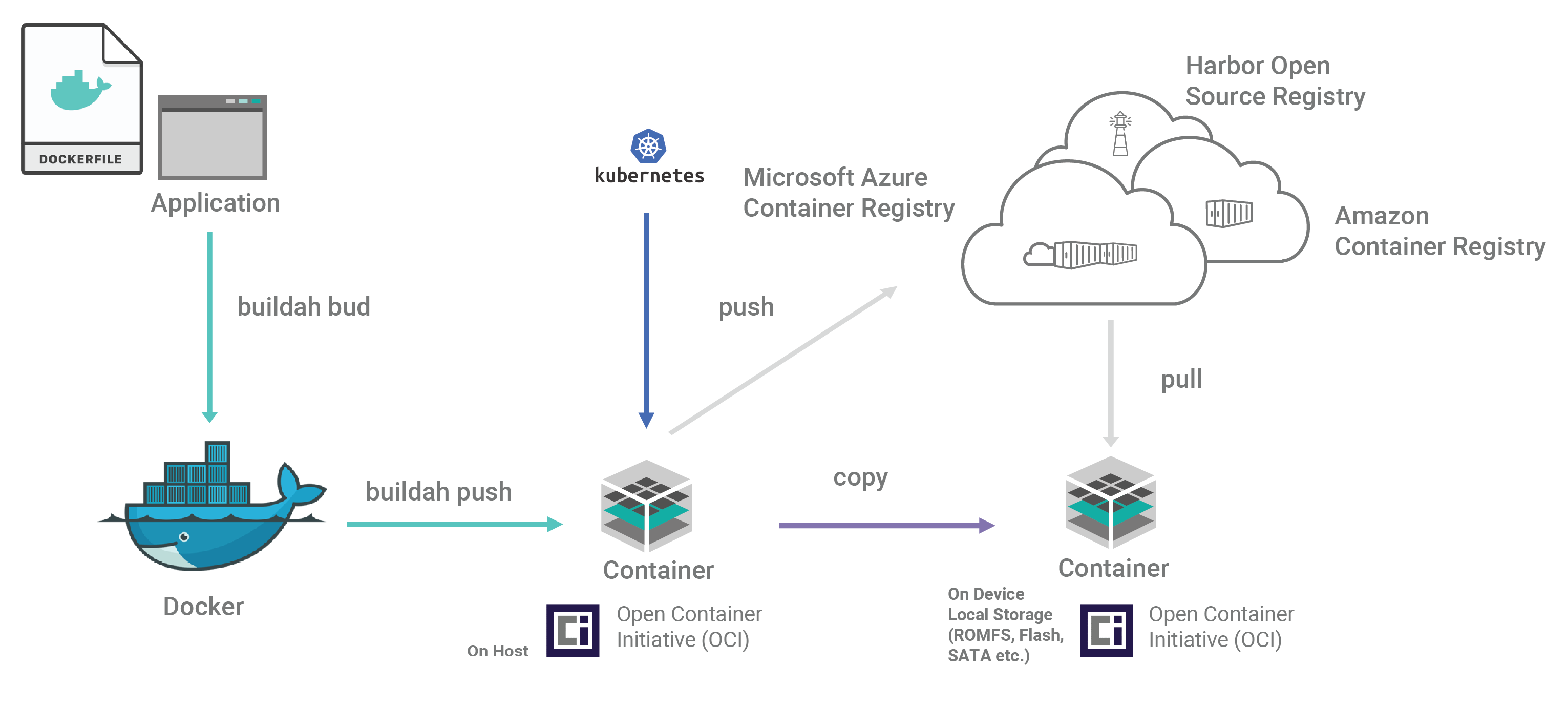
Figure 2: End-to-end workflow for creating and distributing containers
Container Security
If container technology is to become successful in environments that call for heightened security — such as aerospace and defense, automotive applications, energy grids and subsystems, robotics implementations, and so on — extra measures for hardening solutions are needed.
Cloud-native, open source registries typically provide a layer of security when using containers. For example, Harbor employs policies and role-based access control to secure container components. Each container image is scanned to ensure that it is free of known vulnerabilities and then signed as trusted before distribution. For sensitive, mission-critical deployments, Harbor provides a level of assurance when moving containers across cloud-native compute platforms.
Only 45% of global security tech leaders say their company has sufficient security policies and tools in place for use of containers.
Following DevSecOps software development best practices is one of the most effective means of protecting container security. The Department of Defense has published the Container Hardening Guide, which outlines DevSecOps processes that are important for guarding against security breaches.
How Can Wind River Help?
VxWorks
VxWorks is the first real-time operating system (RTOS) in the world to support application deployment through containers. The latest release of VxWorks includes support for OCI containers, enabling you to use traditional IT-like technologies to develop and deploy intelligent edge software better and faster, without compromising determinism and performance.
» Learn moreWind River Linux
Wind River Linux includes container technology that supports development and orchestration frameworks such as Docker and Kubernetes.

Our team brings decades of experience in hardening the security around embedded devices to protect them from cybersecurity threats.
It is Docker compatible under OCI specifications, but it is also lighter weight and has a smaller footprint than Docker, which is often a vital need for embedded systems. Delivering a Yocto Project Compatible cross-architecture container management framework, Wind River Linux helps ease and accelerate the use of containers for embedded developers.
» Learn moreWind River Helix Virtualization Platform
Wind River Helix™ Virtualization Platform enables heterogeneous systems employing a mix of OSes and requiring determinism and safety certification to leverage the scalability of containers while meeting the often stringent requirements of embedded systems.
» Learn more