In today’s world of heightened cybersecurity risks, Wind River® has committed to delivering trusted products, services, and partnership to our customers, the industry, and authorities. We ensure the security of intelligent systems from the cloud to the edge with whole-company readiness of integrated and operationalized systems that are aligned to industry security standards, frameworks, and regulations. We maintain a culture of trust that is a core value of our company and is naturally demonstrated in the way we do business every day.
Secure Development Lifecycle
Wind River supports a secure development lifecycle (SDL) across our products that is enforced by policy and implemented with standards, processes, and procedures. The SDL is aligned directly with the NIST 800-218 Standard and its principles: prepare the organization, protect the software, produce well-secured software, and respond to vulnerabilities.
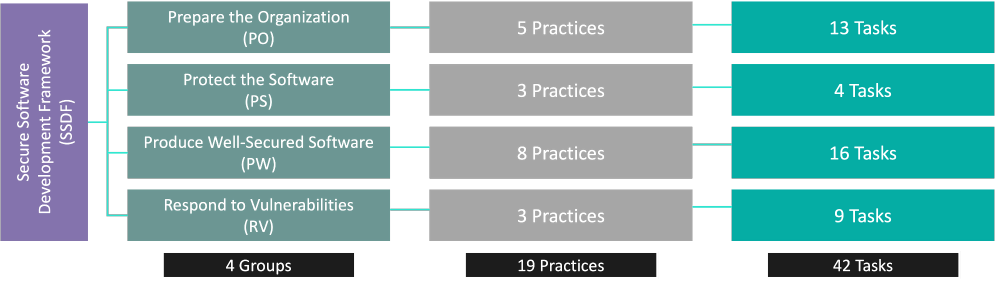
Figure 1. The Secure Software Development Framework (SSDF)
The SDL is tightly integrated with our product development lifecycle (PDLC), and it is deployed across our enterprise and assessed regularly for conformance and assurance to customers of our trusted products.

Prepare the Organization
Wind River supports a product security organization with product-wide security governance, including:
- Enterprise infrastructure certified and externally audited to ISO/IEC 27001:2013
- Development environments, tools, and endpoints hardened and maintained to our information security standards
- Security Champions and Security Training programs for secure outcomes across our products
- Robust policy frameworks aligned to industry standards and mobilized through internal standards, processes, and procedures
- Evaluation and security of third-party components equal to native-developed components in our SDL

Protect the Software
Wind River manages our development environments for least-privilege authorization for assuring that environments, code, artifacts, and tools are accessible only to those who require access, with assurance of the correct access levels. Development, test, and release code provenance data and integrity checks are retained, protected, and communicated to customers with releases.
Wind River provides a software bill of materials (SBOM) of open source components’ Software Package Data Exchange (SPDX) data with General Availability (GA) releases, according to our OpenChain certified process. We also work with our customers on optional SBOM features for their solutions.

Produce Well-Secured Software
Wind River acquires software components from vendors under contract with security agreements and acquires open source software from trusted repositories. These third-party software components, along with internally developed software, are subjected to the full SDL described here to assure the security of all components. These trusted components are enrolled in the standard and trusted repository and authorized for use in the tools, development, testing, and release pipelines.
Ongoing threat modeling is performed using STRIDE, OWASP Threat Dragon, or ATASM to identify architectural weaknesses and systematically prioritize treatments and software features tightly aligned to our overall requirements management process.
Software undergoes independent review by our Security Architects and Security Champions, who check the design, secure coding standards, and risk treatment outcomes. They also establish security baselines for our products that are communicated to our customers in the form of robust software compilation, configuration, and security hardening guidelines.
Throughout the software pipeline, the software is rigorously tested for security use cases, static analysis, dynamic analysis, vulnerability scans, penetration testing, and fuzz testing, with strict management of issues and resolution according to standard issue management and product acceptance criteria.

Respond to Vulnerabilities
The Wind River Product Security Incident Response Team (PSIRT) works with customers, authorities, the security community, and our Product Security Office for SDL polices and standards that empower our development teams and Security Champions with processes and procedures to identify and resolve, in a timely manner, supported product security issues, aligned to the FIRST.org PSIRT Services Framework and the ISO/IEC 30111 and 29147 standards.
Wind River continually provides timely resolution and notification of vulnerabilities and remediations for our actively supported products with security bulletins and a comprehensive vulnerability database accessible from our Security Center.
Note: Vulnerability remediation service levels are provided according to the applicable product license and support and maintenance agreements.
Secure Development Lifecycle
Wind River offers Secure Software Development Conformance statements to customers, providing assurance of conformance to the SSDF. These statements provide customers with supply chain and component assurance that supports their industry-specific integrations, compliances, and certifications across many SDL standards and industries, including:
- ISA/IEC 62443 (operational technology)
- ISO/SAE 21434 UNECE WP.29 R155 and ISO 24089 (vehicle cybersecurity)
- IEC 81001-5-1 (healthcare)
- PCI-SSLC (payment card)
- O-RAN Security Requirements Specification (telecom)
- CIS – Control 16 (aerospace and defense)
- NIST Cybersecurity Framework (CSF) (general and government)
- ISO 20243 (trusted technology providers)
- OWASP SAMM, BSIM (generic SDL maturity)
In addition to our standard product offerings, Wind River provides a wealth of security services to meet your industry-specific needs.