Securing Linux Devices at the Edge: 5 Best Practices to Mitigate Risk
The expanding connected universe offers endless opportunities for cybercriminals and hacktivists to exploit. Security company Kaspersky measured 1.51 billion IoT breaches in the first half of 2021 alone.3 Securing IoT and edge devices requires a unique approach that differs from traditional network and endpoint security. Additionally, there are special security considerations around IoT and edge devices that run on an em bedded Linux platform.
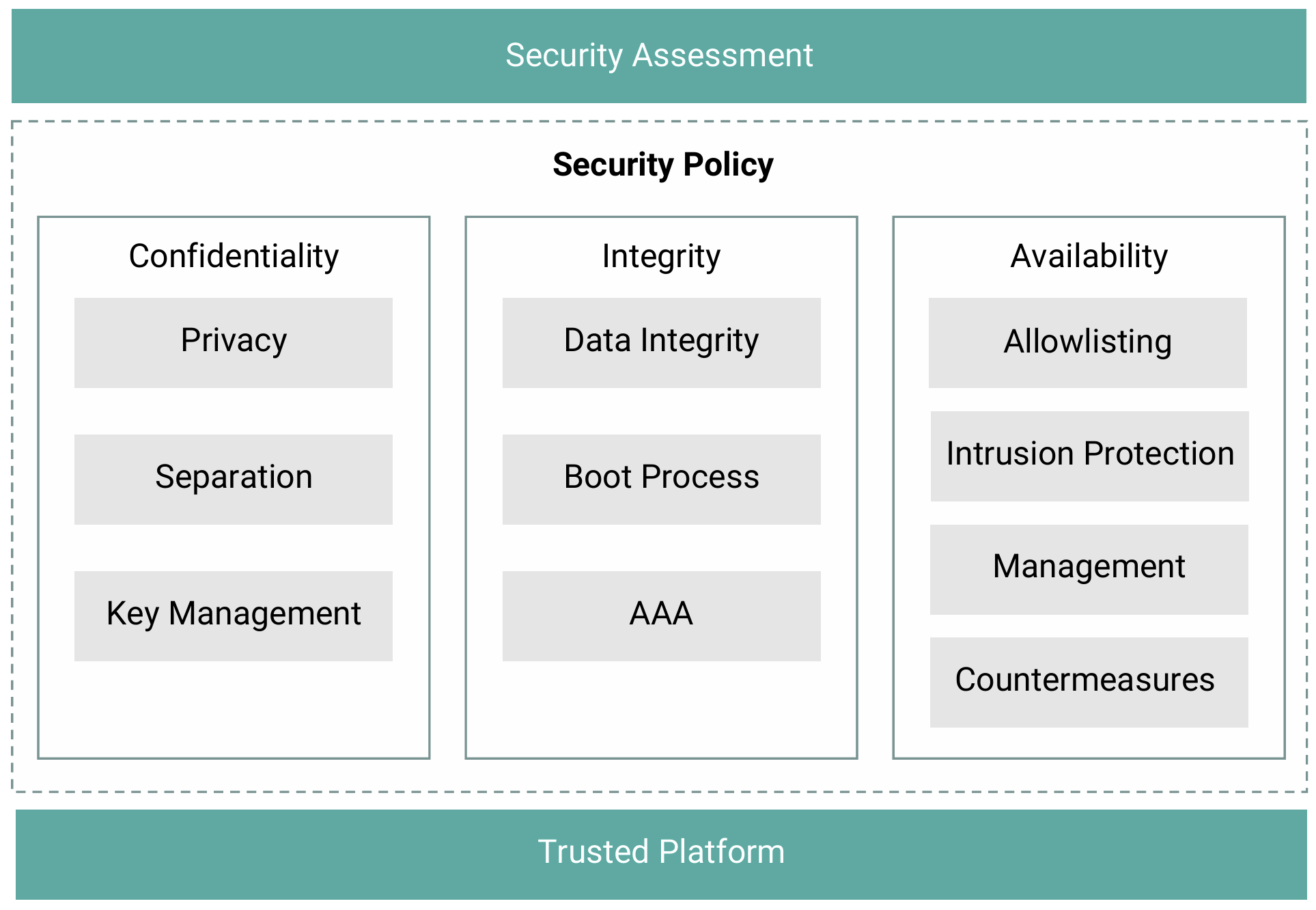
In this white paper, we’ll take a closer look at security best practices for protecting Linux-based devices at the edge, distilled from the decades of Wind River® experience in building, supporting, and securing embed ded Linux devices. Specifically, we’ll examine the five best practices for securing Linux devices at the edge: understanding the threat landscape, securing the data, staying current with security updates, automating the security process, and managing the security lifecycle.
Understanding Your Threat Landscape
A threat landscape is defined by the total number of cyberthreats that can poten tially impact your business, whether the goal of those attacks is data exfiltration, business disruption, extortion, or something else. The first best practice for securing edge devices is to understand which threats can affect those devices. This can be accomplished by focusing on six key questions:
1. What are you protecting?
The most common answer here is data, but you need to dig a level deeper and ask yourself what kinds of data need protection. It could be personally identifiable information (PII), passwords, security data (e.g., encryption keys), device configuration data, and even device-specific data such as the calibration settings on an X-ray ma chine. Beyond that, you may also be protecting people, your business, or the devices themselves.
2. Which specific threats do you face?
Cyberattacks can take many forms, including unauthorized access, data theft, loss of reputation, and financial theft. Threat identification means not only answering the question of what cybercriminals are after but also deter mining the type of threat they pose and which common vulnerabilities and exploits (CVEs) they are likely to target.
3. How much risk can you tolerate?
Weighing risk helps you prioritize security efforts. How would data theft affect your business reputation? What happens if an edge device stops working? Could modifying calibration data on an X-ray machine cause harm to a patient? These are the kinds of worst-case scenarios that businesses need to think about when planning a security strategy.
4. Are you bound to regulations or compliance?
Many industries are regulated by federal agencies, industry watchdogs, or simply their own standards for security. It’s important to understand what the consequences are — financially and operationally — if your security efforts fall out of compliance.
5. How will you respond to a cyberattack?
Do you have a security playbook that is frequently updated to guide your actions in the event of a cyberattack? Without one, your response may be reactive and chaotic.
6. Who will respond to a cyberattack?
In addition to identifying your actions in the event of a cyberattack, you’ll also want to identify your actors. In the case of Linux-based platforms, open source solutions are common, so you may want to include third-party suppliers, community members, and government agencies such as the Cybersecurity Infrastructure & Security Agency (CISA) in addition to your own internal response team.
Automating the Security Process
There were 25,000 unique CVEs identified in 2022,4 and even a critical CVE can take months for the typical organization to fix.5 An automated vulnerability scanner can save thousands of hours and secure more of your threat landscape, faster.
That’s why our fourth best security practice is having an automated vulnerability scanner. We consider it so important that Wind River® offers an automated vulnerability scanner for free.
While free is a compelling concept all by itself, here are 10 more reasons why the Wind River Studio Linux Services auto mated vulnerability scanner can help protect your Linux devices at the edge:
- CVE lifecycle management: Our tool integrates seamlessly into your development lifecycle so you can easily identify, assess, prioritize, and remediate (or mitigate) vulnerabilities and reassess/rescan for vulnerabilities later.
- Accuracy: Automatically tap into upstream CVE resources and curate data to your specific market or source so you can be sure of using the latest, most accurate information.
- Community updates: Leverage the latest security information from upstream sources and community members, including updates about the most recent CVEs and known fixes
- Automated scans: Set scanning automatically (hourly, daily, weekly) and alert security actors with real-time and on-demand notifications.
- Efficient triage: The Wind River vulnerability scanner tool displays CVE data in an easy-to-understand format, including package name/group, license information, color-coded severity, and more so you can more efficiently triage CVEs.
- License identification: Because open source components are common in edge-based Linux devices, you’ll instantly see which licenses are being used in your platform.
- DevOps integration: The Wind River security scanning tool is designed to easily integrate into most CI/CD pipelines.
- Dashboards: The dashboard clearly displays data on environmental health, CVEs, and more so that decision makers can quickly find the answers they need.
- Reporting: The artifacts generated by our vulnerability scanner tool can be quickly exported into several formats (e.g., CycloneDX, Microsoft Excel) for convenient reporting
- Secure software bill of materials: The scanner tool generates a secure SBOM that is protected against unautho rized access.
References
- Hasan, Mohammad, “State of IoT 2022: Number of Connected IoT Devices Growing 18% to 14.4 Billion Globally,” IoT Analytics, May 18, 2022
- Hojlo, Jeffrey, “Future of Industry Ecosystems: Shared Data and Insights,” IDC, January 6, 2021
- Cyrus, Callum, “IoT Cyberattacks Escalate in 2021, According to Kaspersky,” IoT World Today, September 17, 2021
- CVE Details
- Marshall, David, “Latest AppSec Stats Flash Report from NTT Application Security Finds 50% of Sites Vulnerable in 2021,” VMblog.com, February 18, 2022