ウインドリバー | ウェビナー&イベント
ウェビナー&イベント
最新の組込みソフトウェアの動向や技術に関する
イベントやオンデマンドウエビナーをご覧ください。
最新の組込みソフトウェアの動向や技術に関する
イベントやオンデマンドウエビナーをご覧ください。
Embedded systems security is a design methodology, implementation, and commitment that companies embrace to limit the threat exposure of the devices they build and the data these devices generate. Security for embedded devices is a full lifecycle responsibility. It starts well before the first line of code is written, includes protection in case a device falls into the hands of attackers, and continues until a device has been decommissioned.
IDC estimates that by 2025, there will be more than 55 billion connected devices.
Every company should have a security policy in place before an embedded project is approved and started. A security policy is a written and agreed-upon strategy and plan to address the full lifecycle security needs of the product and its data, including design, testing, delivery, maintenance, and decommissioning at end-of-life. Project teams need to fully understand the risks associated with a security breach that impacts their product. In addition, security requirements need to be agreed upon for the individual devices, the communications between devices, the network, and the data.
Similar to IT systems, an embedded security policy uses the CIA triad as a model for policy development. The CIA triad defines the principles needed to protect a device from unauthorized access, use, disclosure, disruption, modification, or destruction. This model helps development teams think about the different aspects of security for their project. The CIA acronym stands for confidentiality, integrity, and availability.
Confidentiality implementations are used to protect the privacy of data in embedded systems. This includes data in motion, data at rest or stored on the device, data being processed by the device, and data passing to and from the device.
Integrity implementations ensure that the embedded device data has not been modified or deleted by an attacker. This includes data being generated or consumed by the embedded device as well as its programming data (the operating system, applications, configurations data, etc.).
Availability implementations ensure that an embedded device performs its intended function. This means an attacker cannot change a device’s intended functional purpose. This is of paramount importance to devices that perform life- or mission-critical tasks.
A security assessment provides a systematic approach to defining protection for the various assets of a project. Wind River® Professional Services offers security assessments for embedded customers starting a new project; these assessments include a variety of security characteristics:
As embedded systems, IoT devices, and the intelligent edge grow in numbers of deployments and new use cases, so does the attack surface and potential for security breaches. Every connected device, from small IoT home thermostats to the most sophisticated systems of systems, holds one or more potential points of entry that can be exploited by a cyberattack. With billions of devices already connected and tens of billions more coming, securing devices and protecting the data they generate is imperative.
In the embedded industry, there is a high degree of trust that companies are adhering to and implementing the most up-to-date standards for security requirements and functionality. For embedded systems with mission-critical and safety-critical applications, a comprehensive and full lifecycle security architecture is essential. Without a security-first policy, no device can be truly secure and remain secure over its deployed lifetime.
Security for software development
The software development infrastructure, where code is developed, tested, and compiled, requires extra security safeguards to ensure that there are no opportunities for either internal or external malicious actors. Many embedded developers use DevOps tools and building blocks from multiple sources. These tools and building blocks should come only from trusted sources and should include a software bill of materials. The components of the development environment should be actively monitored for CVEs and events that violate the system’s security policy. In addition, the development infrastructure should provide strict identity management and access protection to authorized individuals only. Privileged actions within the system should require multiple parties’ approval and performance.

Designing a secure embedded system is a full lifecycle process, starting before the first line of code is written.
Security for Devices — Hardware and Operating System Software
The software and hardware used for embedded devices can include built-in security functionality. Some of the most commonly enabled hardware security features include secure boot, attestation, cryptographic processing, random-number generation, secure key storage, physical tamper monitoring, and JTAG protection. To fully leverage the hardware features, operating system software requires device drivers specific to the architecture of the underlying processor.
Operating system software can also come with built-in security functionality. The VxWorks® RTOS includes built-in security features for secure boot (digital signed images), secure ELF loader for digitally signed applications, secure storage for encrypted containers and full disk encryption, kernel hardening, and much more. (See the VxWorks datasheet for a full list.)
The Linux operating system also provides a number of security packages developers can use to help secure their OS platform build. Wind River Linux, a commercially provided Yocto Project–based build system, includes more than 250 verified and validated security packages. The Linux operating system can also be hardened to provide anti-tamper and cybersecurity capabilities.
Security for embedded applications and container-based applications
Embedded applications are the software designed to perform the function or specific task of an embedded system. Embedded applications run on top of the embedded operating system. Even if the underlying OS is secure, applications can require additional security features, including security testing, the use of code-scanning tools to improve security, and constant monitoring and prompt fixing of security issues.
Container-based applications are starting to be used in embedded systems. These applications are constantly processing data, generating log files, and caching files. Application of critical security controls are put in place to ensure that application activities are not malicious.
Security to protect data
Embedded systems, IoT devices, and intelligent edge systems all process, store, and transport data. Mission-critical and safety-critical applications rely on the integrity of the data to perform intended functions, so it is essential that the embedded system has the right security functionality to prevent data leakage. This means the data, whether in motion, at rest, or in use, is fully encrypted and protected.
Security services
Security is an ongoing effort for embedded systems. It is a full lifecycle activity, from design to decommissioning. For many companies, monitoring and maintaining a device’s security posture for its full life can be best served by leveraging a third-party entity. Managed security services and security as a service are quickly becoming viable options for resource-constrained teams to get the help they need to detect and respond to threats, continuously monitor and analyze deployment operations, and make data-driven decisions to prevent attacks.
Embedded security is designed to protect the components and software of the device. It includes features to protect the hardware, operating system, application, and data. Cybersecurity refers to additional security features that protect a device from network-initiated attacks. Both forms of security are necessary for embedded systems, IoT products, and intelligent edge devices.

Both embedded security and cybersecurity are necessary for reliable embedded device performance across a range of industries.
The DoD provides guidelines for both device security and cybersecurity.
The FDA provides cybersecurity best practices for medical device manufacturers at www.fda.gov/medical-devices/digital-health-center-excellence/cybersecurity. Proof of meeting security requirements can be required to get FDA approval of a connected medical device.
NIST provides security standards and guidelines for a variety of embedded segments, including electronics, energy, manufacturing, and transportation.
FIPS are U.S. government computer security standards specifying requirements for cryptographic algorithms. FIPS 140-3 is commonly followed in the embedded industry.
STIGs are configuration standards consisting of cybersecurity requirements for specific technologies.
Wind River provides a comprehensive security framework for the entire lifecycle of an embedded device. The framework includes a combination of security technologies and services and provides enhanced security capabilities for the development environment, DevOps pipeline building blocks, built-in operating system security features, OS and application hardening, data encryption, and ongoing vulnerability monitoring and fixes.
The market-leading real-time operating system includes numerous built-in security features to protect the confidentiality, integrity, and availability of an embedded device. These features help customers achieve purpose-driven critical safety certifications and standards required for commercial deployment approval.

Wind River offers comprehensive security for the entire embedded device lifecycle.
The leading commercial Linux build system for embedded systems, Wind River Linux includes hundreds of validated and verified security packages. Wind River Linux is fully supported and comes with active monitoring and fixes for CVEs.
Wind River Helix™ Virtualization Platform consolidates multi-OS and mixed-criticality applications onto a single edge compute software platform, simplifying, securing, and future-proofing critical infrastructure solutions in the aerospace, defense, industrial, medical, and automotive markets.
Wind River Simics® is a full-system simulator of hardware and complex electronic systems. Simics can be used to test security vulnerabilities and security breach scenarios in a safe and controlled environment.
Professional Services provides deep industry experience to plan and design security into the full lifecycle of embedded systems.
In the overall safety of a system or piece of equipment, functional safety is the element that relies on automatic protection operating correctly and predictably in response to inputs or failures. It must be able to handle worker error, hardware failure, and a fluctuating operating environment. Functional safety applies to any segment (aviation, automotive, industrial, medical, transportation, and others). Its goal is to protect humans from injury or death and to prevent life-threatening damage to equipment and facilities.
A mission-critical system cannot fail. Autonomous vehicles with crash sensors must not kill people, for example. The safety of lives is the basis of all functional safety certifications.
In a world that is increasingly connected, data sharing and telematics availability are critical for connecting and updating mission-critical systems and devices.

Autonomous equipment must react to environmental cues to function safely around people and other machinery.
If you have a connected autonomous system, or any connected system, you must prove that its safety-critical elements are secure, or you run the risk of a malicious actor interfering with system safety and the integrity of your data.
To address the challenges and achieve success with these systems, users must bring together platforms with different types of operating systems. The safety-critical features of real-time operating systems added to an open source Linux-based solution can address the software-centric functions of a future that is more automated, autonomous, and statistical.
The next generation of embedded devices is being built with cloud-native technologies that allow companies to explore new use cases at the edge. Today, embedded systems and the applications they run are leveraging the processing power of the cloud and artificial intelligence (AI) and machine learning (ML) technologies to enable greater insights and decision-making at the edge of the network, where devices are deployed.
Operational and environmental data gathering from the intelligent edge is used to improve functionality, ensure safety, and make real-time business decisions.
A mission-critical system cannot be functionally safe if it isn’t secure. End-to-end security for updates, control, and feedback is crucial.
Safety means no injury or loss of life is caused, whether deliberately or not. Security means that people, facilities, operations, data, and more are protected from loss, interference, theft, or negative changes, and that no deliberate harm is caused. Another way of putting this is that safety means protecting the world from the system, whereas security means protecting the system from the world. Both are crucial, but a system cannot be functionally safe if it isn’t secure.
Functional safety in systems, equipment, or devices is essential for safeguarding human lives and preventing human injuries or environmental damage. Its purpose is to use specifically designed hardware equipment and/or software systems that operate to automatically prevent life-threatening, injury-causing, dangerous failures, or that control or halt such failures if they occur so as to stop further danger or threats.

As humans increasingly interact with autonomous or semi-autonomous systems, automatic safety functions become an essential part of the end-to-end system.
The all-encompassing objective of functional safety is to prevent risk to human lives caused either directly or indirectly from the operation of a hardware or software system. This includes preventing risk caused by damage to equipment, property, or the environment. The critical factor at play is the appropriate and correct implementation of one or more built-in, automatic protection functions known as safety functions, which constitute a safety system or safety-related system.
The scope of functional safety is end-to-end, in that it must treat any function of a component or subsystem as part of the operation of the entire system’s automatic protection function. Thus, although the standards for functional safety focus on electrical, electronic, and programmable systems, in practice functional safety methods must extend to the nonelectrical, nonelectronic, and non-programmable components of the system.
To deliver functional safety is to provide assurance and evidence that a hardware or software system meets the properly specified functional safety requirements through certification via the appropriate testing and accreditation bodies.
Any claim of functional safety for a component, subsystem, or system should be independently certified to the proper recognized functional safety standards. A certified product can then be claimed to be functionally safe to a particular safety integrity level (SIL) or performance level (PL) in a specific range of applications. The certificate and the assessment report that describe the scope and limits of performance are provided to the customer.
Certifications should be completed by independent organizations with experience and strong technical depth (electronics, programmable electronics, mechanics, and probabilistic analysis). Functional safety certification is performed by accredited certification bodies. Accreditation is awarded to a certification organization by an accreditation body. In most countries there is one accreditation body. In the United States, the American National Standards Institute (ANSI) is the organization for functional safety accreditation. In the United Kingdom, the United Kingdom Accreditation Service (UKAS) provides functional safety accreditation.
There are functional safety standards for various industries, including aviation, automotive, industrial, medical, transportation, and more. For the industrial sector, IEC 61508 is the functional safety standard. Functional safety certification programs for IEC 61508 standards are offered globally by several recognized certification bodies, including Intertek, SGS, TÜV Rheinland, TÜV SÜD, and UL.
Other functional safety standards that have been derived from IEC 61508 include international standards IEC 62304 for medical device software and the ISO 26262 road vehicles functional safety standard for automotive equipment for all automotive electronic and electrical safety-related systems. For railway transportation, there is EN 50126/8/9.
For the aviation market, the U.S. Federal Aviation Administration has enacted a similar process for functional safety certification. Known as RTCA DO-178C for software and DO-254 for complex electronic hardware, these are applied throughout the aerospace industry. For Europe, the corresponding certification is EURICAE ED-12C.
DO-178C, Software Considerations in Airborne Systems and Equipment Certification, is the principal document that the FAA, EASA, and Transport Canada certification agencies use to review and approve all commercial software-based aerospace systems.
DO-178C by itself does not guarantee safety aspects of the software running in a system. In the system design, the safety attributes and their functions must contain and conduct mandatory additional system safety tasks to implement and demonstrate clear and objective evidence of meeting the specific safety requirements. As specified by DO-178C and as required by the certification authority bodies, the correct Design Assurance Level (DAL) must be established using comprehensive analysis to establish the software level A–E. Any software that commands, controls, and/or monitors safety-critical functions should receive the highest DAL, Level A.
ARINC 653 (Avionics Application Standard Software Interface) is a software specification for space and time partitioning in safety-critical avionics real-time operating systems. It allows the hosting of multiple applications of different software levels on the same hardware in the context of an integrated modular avionics (IMA) architecture.
IEC 61508 is the industrial functional safety standard.
ISO 26262 is the functional safety standard in the automotive industry.
EN 50128 is the functional safety standard for software for railway control and protection.
EN 50129 is the functional safety standard for railway safety-related electronic systems for signaling.
The international standard IEC 62304 specifies lifecycle requirements for the development of medical software and software within medical devices. It has been adopted by both the United States and the European Union and so can be used as the benchmark for compliance with regulatory requirements in both these markets.
The future will be autonomous. How can our platforms evolve and continue to solve customer challenges while incorporating software-centric features such as machine learning and computer vision — all while maintaining safety criticality in a connected world?
Any device or system that is mission critical will also need to be safety certified. If you need to guarantee that the brakes function or that the ailerons will work, you will need a real-time operating system that is certified for the specific standards within its market, be that aerospace, defense, automotive, industrial, medical, or rail.
You’ll also need functional safety consideration and support applied throughout the product lifecycle, including the legacy-device stage.
Finally, as silicon manufacturers move toward multi-core environments, you will need operating system support for these devices and systems.
To address autonomous middleware and AI challenges going forward, most development will be on Linux. As the most popular development operating system for AI, ML, and DL, it will be critical for minimizing the distro size for devices out in the field.
In a safety-critical use case, however, this means introducing Linux into a system that typically requires an RTOS. A device may require an RTOS for guaranteed performance, for example, but coupled with AI/ML algorithms that are mostly associated with Linux. Developers and customers need applications and systems that span both types of operating systems, and system integrators are needed to work on both sides of this equation.
With modern silicon containing two to eight cores on a single system-on-chip, in today’s complex systems a safety-certified RTOS and an embedded Linux OS are no longer two different control units spanning a network. Instead these two very different operating systems run side-by-side on a single system-on-chip. In this scenario, having a means to monitor both sides with high-speed communication is critical. A hypervisor that is certified, fast, and able to manage the host operating system(s) becomes essential.
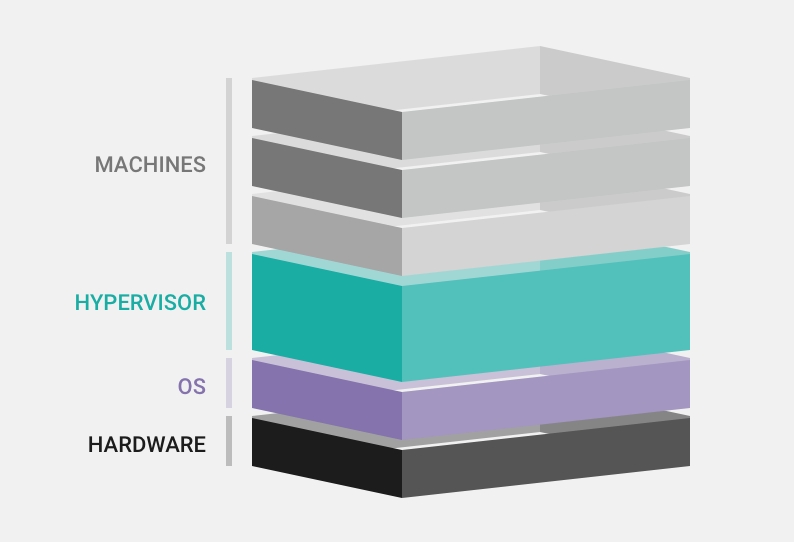
A hypervisor enables multiple operating systems with different characteristics to run on a single system-on-chip.
In the new era of autonomy and connectivity, where it is increasingly important to identify and implement safety-related systems, Wind River® continues to lead the way. Our software runs the “can’t fail” computing systems of the most important modern critical infrastructure, including aerospace and defense, rail, automobiles, medical devices, robotics, industrial control systems, smart factories, and more.
Only Wind River offers the complete set of components that go above and beyond what is available from the rest of the market. We have the class-leading safety-certified real-time operating system; the most common commercial embedded Linux solution, based on the Yocto Project; and a safety-certified hypervisor.
Wind River also has extensive experience meeting the safety-critical standards of crucial sectors, including flight safety (DO-178C DAL A), industrial (IEC 61508), rail (EN 50126/8/9), and automotive (ISO 26262).
VxWorks® has an extensive portfolio in safety certification of software products, including 600+ safety certification programs with more than 360 individual customers, including more than 100 civilian and military aircraft. Its robust safety features provide advanced time and space partitioning capabilities to enable reliable consolidation of multiple applications with different levels of criticality on a single- or multi-core platform. Conformance to standards such as POSIX® and FACE™ have been leveraged in the certification of VxWorks to DO-178C, IEC 61508, IEC 62304, and ISO 26262 safety standards.

VxWorks 653 Multi-core Edition is a safe, secure, and reliable real-time operating system. It delivers an ARINC 653–conformant system by providing robust time and space partitioning on the latest hardware platforms to ensure fault containment and the ability to upgrade applications with minimal test and integration demands.
Wind River Helix Virtualization Platform has been designed to be certified and to simplify the certification of safety-critical applications according to the stringent requirements of the DO-178C Software Considerations in Airborne Systems, IEC 61508 industrial functional safety, and ISO 26262 automotive safety standards. It is an OS-agnostic edge compute platform with a real-time, embedded, Type 1 hypervisor that can manage unmodified guest operating systems running VMs and consolidating the workloads for devices.
Medical Application #1
Medical Application #2
Application #3
Application #4
VM 1 VxWorks
(Safety Critical)
VM 2 Wind River Linux
VM 3 Windows
VM 4 Third-Party OS
(Safety/Non-Safety)
Wind River Helix Virtualization Platform — Hypervisor
Multi-core Hardware
Certification of a system is a complex, costly, and demanding process. The A&D, medical, industrial, and security industries each have their own different but similar safety standards. Wind River Professional Services provides the safety-critical expertise to help you through the certification process.
Wind River offers security and compliance scanning with analysis and remediation services to help you build higher-quality code and accelerate your time to deployment.
Automated security and compliance scanning, tuned for complex embedded software systems, helps developers quickly identify and prioritize high-risk vulnerabilities and license issues. Build higher-quality code and accelerate your time to application deployment.
Scan the health of your Linux platform for all existing CVEs as they emerge. We run our professional-grade scanner and compare it to our extensive database to accurately identify potential vulnerabilities. Our engineers then provide a deep analysis of the true impact on your platform.
Scan your Linux platform to provide a detailed report of all the licenses used in your platform as well as transitive dependencies.
Work with our global team of engineers to quickly identify and prioritize vulnerabilities based on a common vulnerability threshold (CVSS), severity of impact, and difficulty of attack and avoid ability. We work with you to build a mitigation plan to address prioritized CVEs.
Our team of engineers performs a deep analysis to determine the impact of the restricted licenses used in your solution. We work with you to prioritize remediation options and timing.
Our team of engineers performs a deep analysis to determine the impact of the CVE on your Linux platform. We work with you to prioritize remediation options and timing. We backport, validate, and verify community-based patches before we apply them to your code. If a community solution is unavailable, we work with your engineering team to architect a technical solution.
Our team of engineers performs a deep analysis to determine the impact of the restricted licenses used in your solution. We work with you to prioritize remediation options and timing.
We ensure you have a high-quality and stable Linux platform, and all remediation efforts enter the Wind River continuous integration (CI) pipeline for a nightly/weekly/monthly build and test process throughout development. After remediation testing and release, Wind River will generate a new software bill of materials and documentation that can be used for project verification.
A new software bill of materials is generated after every code modification.
Wind River can be your partner and voice for the Yocto Project.
We can work on your behalf to upstream and contribute any fixes or engineered resolutions back to the
community.
Wind River has a global team of experts to support your Linux platform. Additional support options are
available.
» See Awards and Industry Recognition for
Wind River
Wind River is a founding member of the Linux Foundation’s Yocto Project.
We are one of the top contributors and maintainers of several key components.
» Learn about the Yocto Project
In the embedded industry, the lifecycle of a Linux product can last 5, 10, or even 15 years or more, so the decisions you make now and along the way will impact speed, quality, and resources for years to come. They can also create technical debt and directly impact future scalability, profitability, and the overall success of your project.
≫ Read MoreThreat modeling is a process for thinking through, identifying, and documenting known threats and mitigations to a system before that system is deployed. Threat modeling acknowledges that all systems face various threats before, during, and after deployment, and it helps security experts identify and mitigate those threats before they occur.
Threat modeling optimizes application security by:

Threat modeling is a proactive process for addressing system threats
Threat modeling helps us make informed decisions about security postures and risk of cyberattacks. While it is possible to run multiple security scanning tools and separate third-party penetration testing engagements on a system, these occur late in the software development lifecycle, at which time the cost of mitigating threats is much higher.
The benefits of threat modeling for an application can be summarized as follows:
Threat modeling happens during the design phase, which allows threats to be addressed early in the software development lifecycle and lowers the cost of mitigation.
Documenting an application’s security architecture and creating a threat model are key steps in ensuring that an application maintains its security assurances and can defend itself against external threats.
A threat model allows us to take a structured approach to evaluating the security level of an application, prioritize risks, and implement risk-mitigating controls in an effort to reach a state of security assurance that falls within an acceptable risk level.
The process of threat modeling is simple, but it needs to be approached with discipline and care. Since the attack surface of any given system changes as technology changes, and since new threats are constantly emerging, we must understand and acknowledge what we know vs. what we don’t or can’t know about any modern system.
In general, there are three basic approaches to threat modeling: software centric, attacker centric, and asset centric.
A risk mitigation focusing on software:
An approach that highlights the attacker:
Focusing on assets, this approach:
In general, threat modeling methodologies establish a catalog of potential threats that are relevant to adversary tactics and techniques as well as attack frameworks. When possible, technology specifics are abstracted away. Resolution or mitigation of identified threats with appropriate security controls establish the security posture of the system. Many different methodologies can be used, including:
This type of threat model, developed at Microsoft, is software centric (developer focused) and uses the pneumonic STRIDE to categorize threats as follows:
| Threat Category | Property Violated | Threat Description |
|---|---|---|
| Spoofing | Authentication | Illegal access and then use of another user’s authentication information, such as username and password |
| Tampering | Integrity | The malicious modification of data |
| Repudiation | Accountability (Audit) | Associated with users who deny performing an action without other parties having any way to prove otherwise |
| Information Disclosure | Confidentiality | Exposure of information to individuals who are not authorized to access it |
| Denial of Service (DoS) | Availability | Attacks that deny service to valid users |
| Elevation of Privileges | Authorization | Privileged access gained by an unprivileged user, who then has sufficient access to compromise or destroy the entire system |
In the STRIDE methodology, data flow diagrams of the application’s use cases are created by decomposing them to identify system entities, events, and boundaries. Threat categories are then used to apply a general set of known threats to the system and assess the system for mitigations to these threats.
Process for Attack Simulation and Threat Analysis (PASTA) is a risk-based methodology to threat modeling that takes an attacker-centric approach in identifying threats to an application. This methodology follows the seven-stage process shown in the diagram at left.
As PASTA follows an attacker-centric approach, it uses “attack trees” to depict potential attacks on a system in a tree-form diagram. The tree root symbolizes the goal of the attack, and the leaves show ways to achieve that goal. In order to leverage a threat modeling methodology that uses attack trees, one must be familiar with an attacker mindset and capabilities.
The Trike methodology, which is an open source project that uses threat models as risk-management tools, was originally created to improve the efficiency and effectiveness of existing threat modeling methodologies. It was first implemented as a tool in the programming language Smalltalk and is now implemented through spreadsheets.
Visual, Agile, Simple Threat Modeling (VAST) is a threat modeling methodology developed by the creators of the ThreatModeler product. Its purpose is to address the enterprise scalability gap by integrating into the full software development lifecycle (SDLC). VAST incorporates three pillars to support a scalable threat modeling solution:
It is important to note here that VAST was developed to define the way that the automated tool ThreatModeler enables enterprises to threat model at scale. Therefore, full details of the stages of this methodology are not relevant here.
Security Cards is a threat modeling methodology developed by the Security and Privacy Research Lab (CSE) and the Value Sensitive Design Research Lab (iSchool) at the University of Washington, Seattle. Its purpose is to facilitate exploration of potential security threats for a particular system; more broadly, it aims to develop a security mindset. It is based on brainstorming and creative thinking rather than a structured modeling approach.
The Security Cards toolkit provides a deck of 42 cards grouped across four dimensions (or suits):
Each card contains:
It is best practice to recognize that you will never be able to completely mitigate all threats to an application. In some cases, there will be threats that you won’t be able to identify. Techniques developed in the future will add threats to your application that don’t exist now.
The creation of threat models can be guided by a security expert, but the task is not only for security experts or security teams. A comprehensive understanding of the architecture of the system, design decisions, implementation, and engineering decisions is important and necessary to create a complete threat model. This usually means bringing in experts from across the team to help create a complete picture of the system so that all threats, vulnerabilities, and mitigations can be identified.
Threat modeling is too often done toward the end of a development phase, immediately before deployment. This is too late. Threat modeling can and should begin as early as possible in the design of the system and continue throughout design and development. Identifying threats early can help avoid security-problematic design decisions and give development teams time to change the design to a more secure system posture.
Modern tools can test system environments, ensure that they are properly secured, and provide your team with the confidence to work intelligently during the day and sleep peacefully at night.
Wind River® Simics® is a fast, full-system simulation platform that uses scripts to define, link, and execute virtual prototypes. Attacks can be launched automatically by reusing publicly available or in-house proof of vulnerability (PoV) in Python. In addition, simulation can be played back at any time for detailed source code–level analysis with determinism, which provides invaluable insights for threat modeling and documentation.

Wind River Professional Services and products can help identify and mitigate system threats
Wind River Professional Services is a team of experts ready to assist you with threat modeling training or to conduct a threat model of your application, identifying threats and mitigations on your behalf.
Wind River offers comprehensive solution services by industry experts who can interpret requirements, architect options, and provide recommendations.
Starting a Linux project with a binary supplied by a hardware vendor is the fastest and easiest way to get to a proof of concept (POC). But embedded systems typically have unique, market-specific functional requirements. Moving from a POC to a deployable product takes a lot more system architecting, feature integration, and long-term management over the entire lifecycle.
Detailed planning in the initial phase is key to a successful Linux project. This planning should
include full lifecycle scope, defining functional requirements and system architecture, identifying
risks, and creating a detailed project plan.
Wind River® offers comprehensive solution services by an experienced team of industry experts who can
interpret system requirements, architect platform options, and provide recommendations for
meeting business, technical, and program goals. Their engineering expertise can help you accelerate
time-to-deployment, increase quality, lower risk, and ensure greater long-term project success.
Our team of embedded experts can assess the full lifecycle requirements for your project. We look at your design architecture, security and risk tolerance, market specifications, and available hardware and software technologies to recommend a course of action.
Many embedded systems have unique market requirements which must be met before deployment, such as features and customizations to meet specification and standards requirements. In addition, rigid deployment environments can require additional optimizations for performance and footprint.
Work with our team to quickly identify and prioritize the vulnerabilities based on a common vulnerability threshold (CVSS), severity of impact, and difficulty of attack and avoid ability. We work with you to build release plans to address critical and prioritized CVEs and defects.

Wind River is a founding member of the Linux Foundation’s Yocto Project.
We are one of the top contributors and maintainers of several key components.
» Learn about the Yocto Project

In the embedded industry, the lifecycle of a Linux product can last 5, 10, or even 15 years or more, so the decisions you make now and along the way will impact speed, quality, and resources for years to come. They can also create technical debt and directly impact future scalability, profitability, and the overall success of your project.
≫ Read More