Five Sure Bets for Medical Device Developers
Strong Development Methods and Digital Technology for Success
Executive Summary
As new digital technology drives advancement in a wide range of industries, the medical device segment in particular is witnessing the importance of innovation. A 2024 study by McKinsey & Company found that 67% of healthcare leaders recognize the importance of long-term technology investments.1
And with increased investment in digital transformation and R&D, med tech leaders are focusing on modern development methods and ways to deliver more innovation — for example, shifting from manual techniques and nondigital technology to more digital processes, such as machine learning and artificial intelligence — to power medical processes and improve healthcare. According to the World Economic Forum, $1.3 trillion was invested in technology transformation projects in 2022, an instance of more than 10% YoY growth.2
To keep up with the market, medical device companies need to invest in new development methods and digital technology. Wind River® experts recommend a strong set of actions that medical device developers can adopt to succeed in creating new technologies to advance healthcare in the digital era:
- Effectively manage risk throughout the software development lifecycle (SDLC)
- Develop an extensible platform
- Automate everything
- Proactively manage cybersecurity threats
- Adequately secure the data
- Application use case: How this software will be used with the medical systems
- Robustness: How the software enhances or changes the device operation
- Lifecycle management: How to manage bugs and updates supplied from a third party
- Failure: How to address the failure modes of the software
- Community development process: How updates and changes are are made for open system software
- Defect management: The process provided by the software developers for managing defects
- CVE management: Upstream management of common vulnerabilities and exposures (CVEs) when they are newly discovered
- Component management: Managing different components of the soft ware to meet requirements
- Obsolescence/EOL: Understanding and managing the full lifecycle of the software through end-of-life (EOL)
Including use of SOUP guidelines as part of the medical device software development process requires significant effort, time, and resources but helps ensure that the device complies with IEC 62304 requirements.
Develop an Extensible Platform
Next, developers should concentrate on developing an extensive and extensible platform for any medical device. It is not enough to simply develop and release the software with no additional work until end of life; instead, careful planning is required to outline what the device should accomplish throughout its lifecycle. An embedded systems journey is similar to a Linux or open source development journey: From the beginning, as part of the ideation process, a developer must consider needed work with the open source community, licensing, long-term support, security fix updates, and defect management for the device lifecycle.
After the product idea is fleshed out, the developer should create a prototype of the medical device, considering and outlining the answers to questions in at least four distinct areas:
Prototyping
- Evaluate design choices through extensive research, to test and validate hypotheses that answer:
- What key design choices are needed for the medical device’s entire life?
- What are the technical and functional risks?
- What are the approach and test risks of a hypoth esis methodology?
- What are the design decisions to be made?
- How will we evaluate whether the correct deci sions are being made?
- Prove out new technologies by conducting market analyses and building a business case to address:
- What are the new technologies that can aid development of the new medical device?
- Which do we want to use? Is there a market fit?
- How will we determine whether the technology is right for the device?
- How will the inclusion of the new technology impact budget or cost considerations?
- Will using the new technology fit within the devel opment timeline?
- Fine-tune timeline accuracy to communicate it to internal stakeholders and external customers, and to mitigate delivery risks, by asking:
- What are all development and technology ele ments to consider?
- Can the software development work be complet ed to meet the target time-to-market date?
- How do internal and regulatory processes im pact time-to-delivery?
- Reduce overall time-to-market by iteratively and proactively planning ahead to determine:
- What are the key areas of risk?
- How can they be resolved in a manner that will bring the device to market on time?
- What resources, including cross-functional sup port, are needed throughout the full SDLC?
Decision: Build or Buy the OS
A major decision is whether the development team will focus its engineering resources on the medical solution’s differentiators or on maintaining the operating system (OS). Questions to consider when determining whether to build or buy the OS for the medical device include:
- Are we ready to commit to supporting our OS for 10+ years?
- How will we deal with the huge number of CVEs reported each year?
- What kind of staff is required to support the OS?
- How to comply with export and compliance requirements?
- How to deal with the accelerating rate of change?
- What if the development team needs help?
Evaluating these questions will assist your decision to build your own (utilizing open source Linux) or buy a com mercial Linux or real-time OS.
Navigate and Manage Technical Debt
Technical debt occurs when product development teams prioritize speed of delivery over quality for specific func tionality. The results are generally issues with the code or increased difficulty in maintaining the software, and both ultimately increase overall costs. Consider these best practices when navigating technical debt:
- Free isn’t always free: There is a total cost of ownership that comes with the use of open source software. The trade-offs of maintaining and managing open source or free software must be considered.
- Determine the long-term impact: An incomplete understanding of future requirements or needs can result in overlooking important issues that will require additional work or expense at a later date.
- Build in buffers for strategic analysis and alignment: Tight deadlines and pressure can result in decisions and actions that later cause technical debt.
- Don’t skimp on planning: Unexpected requirements changes and scope creep cause delays, increasing rework and driving costs higher.
Automate Everything
An increased focus on automation can help develop medical devices and other new products. Automation has uncov ered long-known but often unaddressed development issues, such as time wasted waiting for tests, builds, and pipeline debugging. When it comes to expertise and infrastructure, only 4% of employees consider their organizations expert in CI/CD,3 while 86% of developers indicate they are experiencing challenges with software complexity.4
Software Complexity
Software complexity combined with the use of a development infrastructure can create challenges for device developers. Using development automation can help solve this problem, and it must be built in from the beginning of the project.
The complexities that development teams need to address include:
- Algorithmic complexity: This requires more expertise and time for development.
- Legacy and open source software: The team might need to develop around older software or ensure that the open source code is up-to-date and/or secure.
- Data analytics and AI/ML usage: Expertise is needed to incorporate these into the medical system.
- Development environment and size of the organization: These can be complex, with multiple developers or devel opment teams working on the project or on a project component.
- Evolving security threats: Since these are a daily concern and priority, security must be built into the development cycle at the start and constantly monitored throughout the product lifecycle.
- Software and device testing: Testing provides great value, but it adds to development timeline and complexity.
Automation Advantages
Automation in software development eliminates manual processes, minimizes errors, and makes development fast er and more efficient overall. It also improves team success by incorporating agile best practices such as CI/CD and DevSecOps. Best-in-class organizations focus on automated builds and testing, and software automation pipelines are the cornerstone of their automation.
- A continuous integration (CI) pipeline automatically builds and tests code changes to ensure compatibility with the existing code base. A continuous deployment (CD) pipeline automates the deployment of validated and tested code changes to staging or production environments.
- DevSecOps is the collection of ideas and practices that assist the workflow automation of CI/CD. It calls for all aspects of software and device use cases to be tested for performance and efficiency. However, it can add to the complexity of the development process and timeline if not implemented effectively.
Adequately Secure the Data
Data is one of the most important outputs of today’s devices, and it is critical that it be adequately secured throughout the device lifecycle. This can be done as shown in the CIA triad, representing the areas of confidentiality, integrity, and availability. Creating new and innovative medical devices and technology requires utilizing modern, comprehensive, and strong software development methods and digital technology.
The five development strategies highlighted in this document should assist in the device certification process and help medical device development teams create devices that are safe, secure, and reliable throughout the entire product lifecycle.
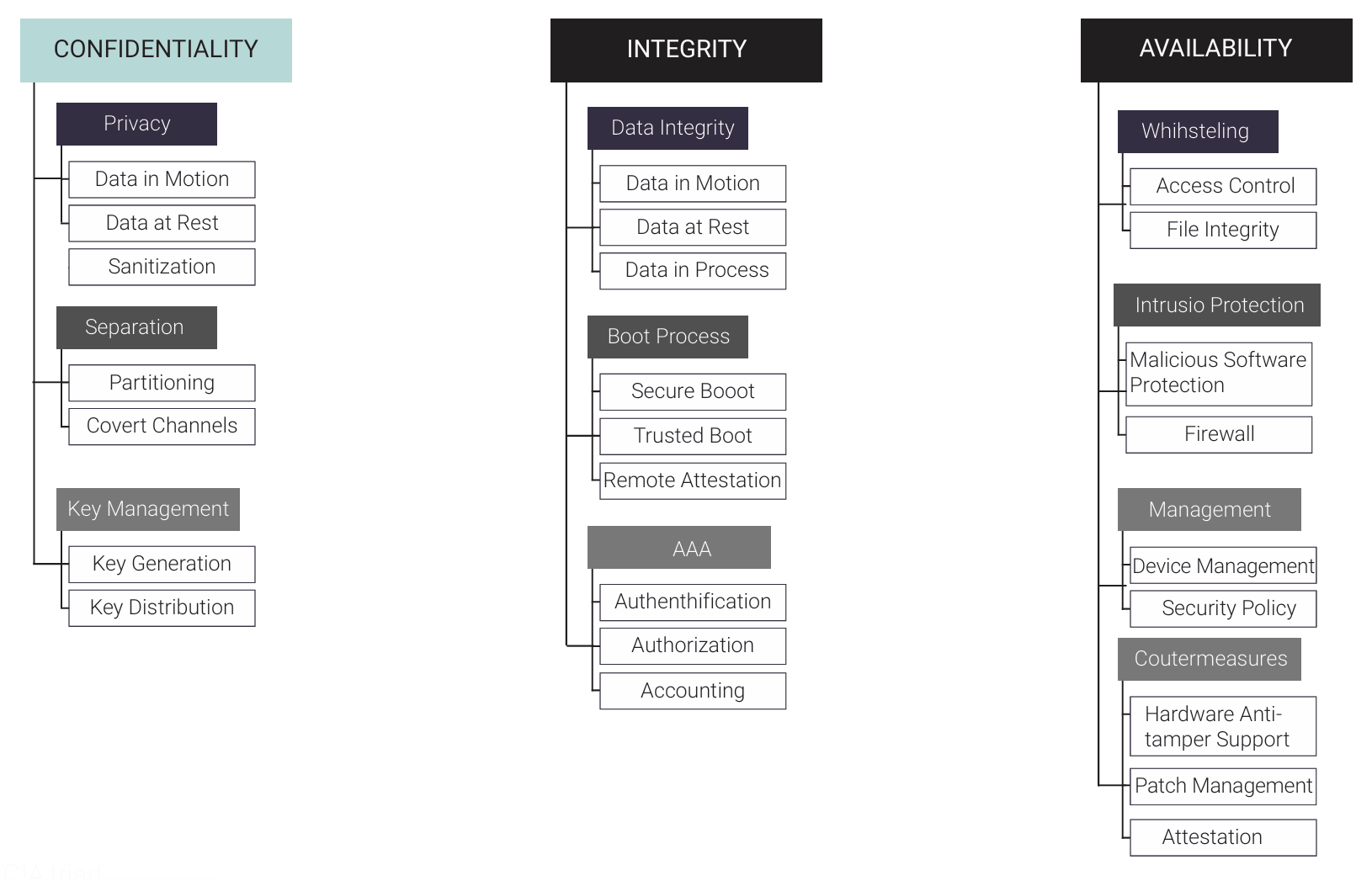
These different security implementations can be layered together to protect the identified assets — in this case, the data from identified threats. While there are many different areas of security management, patch management and cryptographic sanitization are two that have grown in importance and focus with new data protection and data management regulations.
- Patch management plan and system: This must be in place to provide easy updates to a medical device to protect the data, system, medical facility, and, most importantly, the patient. This is a high priority met by recent regulatory requirements for data protection and updates to the device and software system.
- Cryptographic sanitization: This allows all devices to erase all site-specific data, whether that is patient data or proprietary device information. The ability to wipe the data clean prior to retirement of the device or system, so that cryptographic keys are not retrievable, will become increasingly important for the protection of patients and medical facility systems.
References
- McKinsey & Company, “Faster, Smarter, Bolder: How Midtenure CFOs Shift into a Higher Gear,” 2024, www.mckinsey.com/capabilities/strategy-and-corporate-finance/our-insights/
- World Economic Forum, "How Digital Transformation Is Driving Action in Healthcare," 2022, www.weforum.org/agenda/2022/09/health-information-system-digital-transformation-healthcare
- Globenewswire, “New Research Reveals Current Truths About the State of DevOps for Hybrid Cloud,” 2021, www.globenewswire.com/ news-release/2021/08/25/2286392/0/en/New-Research-Reveals-Current-Truths-About-the-State-of-DevOps-for-Hybrid-Cloud.html
- Gartner, “What Edge Computing Means for Infrastructure and Operations Leaders,” 2018, www.gartner.com/smarterwithgartner/what-edge-computing-means-for-infrastructure-and-operations-leaders