Software Security Across the Intelligent Edge
Security Must Cover Every Single Endpoint Device, Through the Entire Lifecycle
Project teams determine which components of the CIA Triad are required based on risk exposure, regulatory requirements, and IP protection needs balanced against cost, performance, and the device deployment operational environment. There is no single silver-bullet solution for protecting a device or system from all possible attacks. Rather, a layering approach that uses different mitigation controls delivers a multifaceted protection shield and, ultimately, a much stronger cybersecurity implementation
Questions to Ask As You Near the Edge
ARE YOU SUCCESSFULLY TRANSFORMING OR INADVERTENTLY EXPANDING YOUR THREAT SURFACE?
Five Security Questions to Answer As You Digitally Transform
As the world of embedded systems and the operational technology (OT) domain become increasingly digital, and as the lifecycle of devices moves beyond fixed-function and break/fix, fundamentally different strategies will be required to securely design, deploy, orchestrate, and adapt the next generation of mission-critical systems.
- Is your security strategy focused primarily on end points or is it a truly system-level approach encompassing the cloud and providing a chain of custody for the data at the heart of digital transformation?
- Do you have an established methodology for the simultaneous development of functionality and the security elements of your IoT systems, and if so does this methodology support the proliferation of threats that come with digital transformation?
- Does your system architecture support efficient management of and updates to edge devices from deployment onward, anticipating the next generation of security threats and affording the flexibility required to ensure security across decades in the field?
- Do your existing enterprise security tools recognize the diverse industry-specific protocols of your IoT systems and, if not, how will you detect intrusion over these protocols as digital transformation accelerates enterprise and edge convergence?
- Does your enterprise security perimeter encompass devices deployed to the field and, if not, how will you ensure secure connectivity between these devices and the enterprise?
IS YOUR DATA IN THE CLEAR?
Three Security Questions to Answer As You Build and Deploy DataCentric Devices
Device manufacturers must embrace the new digital paradigm of interconnectivity and data dynamism, designing in security not only for data in memory or storage but also for data passing through a system or over a network, and for the keys used to encrypt that data. Meanwhile, they must also ensure that software and hardware are hardened against tampering that compromise data integrity. Does your organization have a comprehensive approach to data security and privacy, or are your development efforts focused exclusively on end-point security?
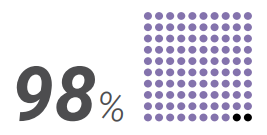
- Will systems you develop be part of the 98% of IoT devices sending data in the clear, or will you encrypt your data?
- Do you have a clear understanding of the deployment environment into which your systems will be fielded, the attacks that environment may be subject to, and how the deployment environment may or may not introduce privacy considerations?
- Do you have a testing strategy to address the full range of threats to data security?
Our technology is in more than 2 billion devices throughout the world and is backed by our industry-leading professional services, award-winning customer support, and robust partner ecosystem.
Our customers can leverage state-of-the-art, robust, and reliable software platforms that protect privacy, maintain data integrity, and ensure availability with seamless system integration and developer collaboration. Our platforms serve as a trusted foundation so you can innovate securely and protect your device against current and future threats.
Our proven secure-by-default platforms and deep industry experience allow you to build your device with confidence on industry-leading technology, knowing private data is protected, critical systems are isolated, and system management is securely built into the ecosystem. This allows you to reduce risk, speed up iterations, and deploy with confidence throughout the product lifecycle.
Security Worksheet for the New Digital World
ARE YOU ORGANIZING FOR A NEW DIGITAL AND VOLATILE, UNCERTAIN, COMPLEX, AND AMBIGUOUS (VUCA) WORLD?
- Are you increasingly working with new design security requirements for your devices?
- Is the VUCA world we live in seen as an asset by the organization, and do security requirements hold you back or accelerate your ability to thrive?
- Is your core security strategy likely to be very different in five years’ time, as you digitally transform as an organization?
ARE YOU SUCCESSFULLY TRANSFORMING OR INADVERTENTLY EXPANDING YOUR THREAT SURFACE?
- Is your security strategy focused primarily on end points, or is it a truly system-level approach encompassing the cloud and providing a chain of custody for the data at the heart of digital transformation?
- Do you have an established methodology for the simultaneous development of functionality and the security elements of your embedded systems and, if so, does this methodology support the proliferation of threats that come with digital transformation?
- Does your system architecture support efficient management of and updates to edge devices from deployment onward, anticipating the next generation of security threats and affording the flexibility required to ensure security across decades in the field?
- Do your existing enterprise security tools recognize the diverse industry-specific protocols of your edge systems and, if not, how will you detect intrusion over these protocols as digital transformation accelerates enterprise and edge convergence?
- Does your enterprise security perimeter encompass devices deployed to the field and, if not, how will you ensure secure connectivity between these devices and the enterprise?
IS YOUR DATA IN THE CLEAR?
- Will systems you develop be part of the 98% of IoT devices sending data in the clear, or will you encrypt your data?
- Do you have a clear understanding of the deployment environment into which your systems will be fielded, the attacks that environment may be subject to, and how the deployment environment may or may not introduce privacy considerations?
- Do you have a testing strategy to address the full range of threats to data security?
DO YOU HAVE THE NECESSARY KNOWLEDGE TO SUCCEED AS YOU NEAR THE EDGE?
- Do you have access to engineering talent with the diverse set of skills required for the development, deployment, and maintenance of today’s IoT devices and related systems?
- Do you have a digital experience strategy that will ensure that your devices are readily operable by a majority Millennial and digital-native workforce?
- Do you have a complete understanding of the supply chain your device fits into — including your software supply chain — and encompassing after-market suppliers?
References
- Forbes/Inc.Digital
- media.nominet.uk/wp-content/uploads/2019/07/Cyber-Security-in-the-Age-of-Digital-Transformation.pdf
- Forbes/Inc.Digital
- The Digital Helix
- threatpost.com/half-iot-devices-vulnerable-severe-attacks/153609/
- www.varonis.com/blog/data-privacy
- Inc.Digital
- www.gartner.com/smarterwithgartner/what-edge-computing-means-for-infrastructure-and-operations-leaders
- Forbes/Inc.Digital
- www.semi.org/en/node/581
- www.cse.psu.edu/~pdm12/cse597g-f15/readings/cse597g-embedded_systems.pdf
- sharedassessments.org/wp-content/uploads/2018/04/2018-IoTThirdPartyRiskReport-Final-04APR18.pdf